
When you watch Criminal Minds, you notice that while the main players share amazingly insightful clues about the Bad Guy ("This is a man, 25-30 years old, blue-eyed, brown hair, short in stature, who was humiliated by his kindergarten teacher, thus he leaves finger-paint prints at the scene of each crime"Â), the real problem-solver is Penelope Garcia, FBI computer mastermind.
She hacks into databases and discovers the criminal record, address, spending habits and color preferences of suspects within seconds, or at the very least, during the commercial break. Criminal Minds may not reflect the types of cyber security we have today, even at a national level, but we're getting there, and you could be the missing link that is needed most in this decade's criminal investigations - the computer forensic investigator.
Cyber Criminals: The New Techno-Bad Guys
Technology is literally everywhere. At an early age (and getting earlier!), children are connected with their family and friends. Laptops, tablets, cell phones, MP3 players, Xbox . . . People now cite their limited time offline as unusual. It stands to reason that criminals would take advantage of this. Many criminal justice careers now include computer forensics (sometimes called "digital" forensics) as an important part of criminal investigating and conviction. Even if a crime is not a "cybercrime"Â (one that is completely computer network- or Internet-based), almost every crime committed these days uses some level of technology. At its most basic, crimes often involve cellphones, where communication data is stored.
Law enforcement agencies have been the flagship developers of computer forensics investigating departments. Computer forensics investigators must follow many of the same practices and procedures as crime scene investigators (CSI). A London-based computer forensics company further defines computer forensics as "collecting, analyzing and reporting . . . digital data in a way that is legally admissible. It can be used in the detection and prevention of crime and in any dispute where evidence is stored digitally."
As a computer forensic investigator, you will have to learn what you can and cannot use “ legally“ in an investigation. It's frustrating, because you might uncover information that proves criminal activity took place, but if you didn't do it in a way that is admissible in court, then you can't use it.
Cybersecurity and Cybercrime
Cybercrime is also when a computer is "the scene of the crime;" for example, hacking, service attacks, government or corporate network attacks in addition to murder, kidnapping, fraud, drug trafficking and human trafficking for sexual exploitation. In those crimes, e-mails, metadata, Internet history, stored documents and files can be gathered for evidence. You were probably watching television or a movie the day you learned that computer-deleted files are not actually deleted.
Your investigative evidence, such as when the information first appeared on the computer, when it was edited, saved, printed . . . all of this is proof that an end user used technology to commit a crime. Computer forensics and cybersecurity often involve crimes that include:
- Bankruptcy
- Corporate, national or international espionage
- Employment disputes
- Federal, state or corporate regulatory compliance
- Forgery
- Fraud
- Theft of corporate or governmental Intellectual Property
- Workplace Internet or emails that are inappropriate
Help Wanted: Computer Forensic Investigator
Computer forensic investigating careers are in their infancy, but as criminal activity becomes increasingly tech-based, the market for computer professionals becomes more demanding. If you want to take your IT knowledge of systems security and management to the next level, if you want to be a trailblazer in the latest technology - or if you're interested in problem-solving and working with the criminal justice system -then becoming a computer forensic investigator could be the career for you. It's a fascinating opportunity.
Forensic job categories include:
- Administrator - Management of a data center team or network security department
- Academia - Research scientist or college-level educator/instructor
- Consulting - Private, independent, salaried or public cyber security analyst
- Engineer - Information systems security
- Financial - Performing due diligence for government or public/private companies
- Law enforcement - Local, state, national or Homeland Security computer professional
- Penetration testing - Isolating cybercrime vulnerabilities within a computer system, network or Web-based app
- Risk assessment manager or analyst
Computer forensic investigators have the advanced skills and training to acquire and compile computer data and electronic communications device information. The ability to recover lost or deleted data is often required. This career can offer a good salary, and the Bureau of Labor Statistics (BLS) reports higher mean wages for forensic investigators on the U.S. east coast.
Become a Cybersecurity Professional
It's kind of like the Wild West era: Computer forensic investigators and cybersecurity professionals will be the marshals of a new frontier. There are no current numbers for the salary median or potential income for this profession. It's that new.
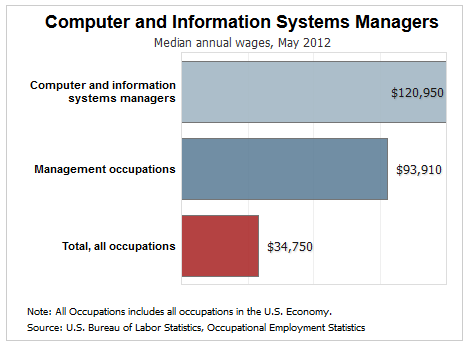 The Bureau of Labor Statistics reported the 2012 median income for Computer and Information Systems managers at $120,950 per year. A master's degree in cybersecurity could prepare you to become a leader in those career opportunities and more! Your advanced information technology science education can lead to administrative and supervisory roles for any size-level company, from Mom & Pop to a Big 10 corporation. It is designed for experienced IT professionals, executives and baccalaureate degree graduates.
The Bureau of Labor Statistics reported the 2012 median income for Computer and Information Systems managers at $120,950 per year. A master's degree in cybersecurity could prepare you to become a leader in those career opportunities and more! Your advanced information technology science education can lead to administrative and supervisory roles for any size-level company, from Mom & Pop to a Big 10 corporation. It is designed for experienced IT professionals, executives and baccalaureate degree graduates.
@ECPIUniversity Network 1 work today. #ecpi #bestdecisionever
- Mark Duffy (@markgduffy89) March 8, 2015
The World of Cybersecurity Awaits
Cybersecurity professionals are leaders and decision-makers. With ECPI University's year-round schedule and online accessibility, you could earn the Master of Science in Cybersecurity degree in as little as 16 months. It could be the Best Decision You Ever Make!
DISCLAIMER - ECPI University makes no claim, warranty or guarantee as to actual employability or earning potential to current, past or future students or graduates of any educational program we offer. The ECPI University website is published for informational purposes only. Every effort is made to ensure the accuracy of information contained on the ECPI.edu domain; however, no warranty of accuracy is made. No contractual rights, either expressed or implied, are created by its content.
Gainful Employment Information - Cybersecurity - Master's
For more information about ECPI University or any of our programs click here: http://www.ecpi.edu/ or http://ow.ly/Ca1ya.


