 If the cybersecurity profession were a book, it would read like a spy novel.
If the cybersecurity profession were a book, it would read like a spy novel.
There are agents setting traps to catch those who hide in the shadows of the Internet, trying to steal data and exploit the vulnerable. There are advanced persistent threats, working against the biggest companies and government agencies. And there is antispyware software engaged to protect the average Internet user.
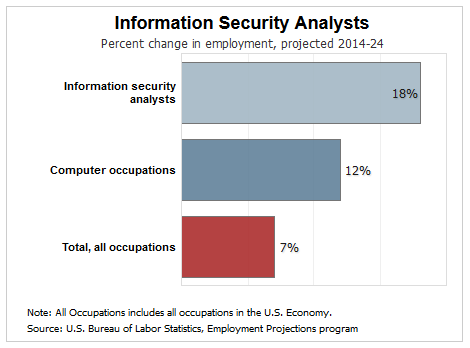 Cybersecurity is an exciting profession that is expected to grow by 18 percent between now and 2024 (according to the United States Bureau of Labor Statistics). And it's always changing.
Cybersecurity is an exciting profession that is expected to grow by 18 percent between now and 2024 (according to the United States Bureau of Labor Statistics). And it's always changing.
And of course, anyone who is interested in pursuing a career as an information security analyst has to have up-to-date knowledge of the industry. Here's a look at five of the biggest cybersecurity trends to keep an eye on in 2016:
Employees with their heads in the clouds
According to a study conducted by Right Scale, which helps companies manage their IT data, the vast majority of companies are using cloud computing. Cloud computing uses a network of remote, Internet-hosted servers to store data. It's economical, easy, and can put these companies at a greater risk of becoming victims of criminal activity.
The move to cloud computing often strips IT departments with much of their ability to oversee and control the way their employees access, download, and use data and software. For this reason, many employees are bypassing their IT departments altogether and downloading tools they think they need. In doing so, they are neglecting their organizations' security protocols and possibly making it easier for people with nefarious intentions to access confidential and private data.
In 2016, as more companies continue to move to the cloud, more employees are expected to dig around in the cloud. Cybersecurity experts help keep employees—and the organizations that offer cloud computing services—in line with their companies' security protocols.
Hundreds of thousands of people held hostage for ransom
It's called ransomware, and each year it costs hundreds of thousands of Internet users hundreds of millions of dollars. Ransomware strikes when people log on to the Internet and suddenly have their most important files encrypted by the malware. The users can't access their data until they pay the ransom.
It's an insidious problem—and it's expected to grow in 2016 (according to the Cyber Threat Alliance, which says that ransomware has cost people more than $325 million).
Tricks with no treats
Criminals have been tricking people into willingly giving up their passwords, bank account numbers, and mothers' maiden names for years. It's called "phishing." But now the criminals are getting more sophisticated, using increasingly clever bait to hook their prey.
These days, they are sending incredibly official looking emails to top business and government leaders, tricking even them—supposedly the best and the brightest—into turning over data. It's a trick that comes with no treats. Cybersecurity professionals will likely play a larger role in educating people about how to avoid these scam artists and protect sensitive information.
Gaining strength through weakness
Companies that don't know where they are vulnerable are more likely to become victims of data theft and other cyber-attacks. That's why 2016 will likely be the year more organizations try to make their cybersecurity systems stronger by being more aggressive about identifying their weaknesses.
According to Hewlett Packard's Cyber Risk Report for 2015, 44 percent of all security breaches in 2014 were due to vulnerabilities that were between two and four years old. That means these companies either ignored the issues for a long time or were unaware of the issues for a long time. Either way, they put their data at risk. This year, cybersecurity experts are likely going to be in high demand to help find the weaknesses and avoid breaches.
Increased connectivity—even for your "things"
These days, you can turn on your lights, start your car and DVR a football game simply by using an app on your cell phone. This phenomenon of connecting everyday objects to the Internet, is referred to as the "Internet of things" (or IoT).
IoT might make life a lot more convenient for the everyday individual, but it can also make it a lot more convenient for criminals to commit their crimes.
Cybersecurity professionals will likely be busy in 2016 helping to ensure that access to everyone's "things" is as limited as possible. But a big job also comes with big opportunities.
It's could be a big year in cybersecurity—and you can be part of it
Yes, the world of cybersecurity is an exciting, ever-changing place that sometimes seems like a spy novel. If you want to be one of the agents that uses their education, knowledge and skills for good, connect with ECPI University today to learn how you can earn a Bachelor of Science in Computer and Information Science with a concentration in Cyber and Network Security in as little as 2.5 years. It could be the Best Decision You Ever Make!
@ECPIUniversity Network 1 work today. #ecpi #bestdecisionever
— Mark Duffy (@markgduffy89) March 8, 2015
DISCLAIMER – ECPI University makes no claim, warranty, or guarantee as to actual employability or earning potential to current, past or future students or graduates of any educational program we offer. The ECPI University website is published for informational purposes only. Every effort is made to ensure the accuracy of information contained on the ECPI.edu domain; however, no warranty of accuracy is made. No contractual rights, either expressed or implied, are created by its content.
For more information about ECPI University or any of our programs click here: http://www.ecpi.edu/ or http://ow.ly/Ca1ya.


